What is our primary use case?
This product is a software-defined data center with a cloud-native approach. We mainly use it for application migration of some of the architecture to containerized solutions.
What is most valuable?
The management platform is great. I really like the management dashboard, the tailor-made assurance, the telemetry, and the ease of integration with all other solutions of VMware, such as vSphere. They also integrate well with other third-party security platforms. It's very easy to give an integration of the cloud tenant of NSX. It's very easy to build and migrate a cloud project.
What needs improvement?
It's very complex. However, I don't work directly with it typically.
We had started two projects for integration with OpenShift and OpenStack with NSX. It was declared by VMware that this is possible, however, the process is very tricky. The full integration was delayed to wait for a new official release. I don't know the actual stage, as this is something that happened more than a year or two ago. It was the beginning of the pandemic. In any case, the integration with OpenShift, the open-source cloud platform, at the time was in need of work and was (and remains) something required from our customers.
They have to work more and more on the integration for public cloud services and have cyber security platform integration.
For how long have I used the solution?
I've been using the solution for about five years.
What do I think about the stability of the solution?
The solution is stable. There are no bugs or glitches. It doesn't crash or freeze.
What do I think about the scalability of the solution?
It seems to scale. However, we don't have enough data in order to say how much clients scale out or the performance when a company is trying to scale out an NSX-T environment. We are not a cloud provider. We don't have a cloud environment to test it.
In terms of who is using it on our side, we have about five to seven people who have the operational capability on NSX-T.
In our organization, we use only a small NSX-T cluster. We have a bigger one for our lab. I can't speak to the usage of our customers where we deployed it.
How are customer service and support?
We're pretty satisfied with technical support.
Which solution did I use previously and why did I switch?
We previously used OpenShift together with OpenStack. It's a different platform. One is open-source and the other is a commercial platform with vendor support and established customers.
How was the initial setup?
The initial setup is very simple. It's not overly complex.
All the VMware platforms are really easy to implement. They require knowledge, of course. However, if you follow the procedure, the output is good.
The deployment itself doesn't take more than two or three days.
That said, we have knowledgeable workers that have done NSX and the previous release (not the NSX-T). They have done deployments several times. That's why, each time, it's really easy to do. If you have to do that in a customer production environment, it will take say no more than one week including both the deployment in production and the training for the customer.
We have three people that can handle deployment and maintenance tasks.
What about the implementation team?
I can handle the implementation myself. We also have trained people inside our organization. We don't need the assistance of integrators or consultants.
What's my experience with pricing, setup cost, and licensing?
I can't speak to the exact licensing costs of the solution.
What other advice do I have?
Most deployments are on-premises or via a private cloud in the case of enterprise clients.
We started several deployments with NSX-T version 3. I can't speak to which version we are on currently.
It works and it is powerful in terms of governance, telemetry, ease of use, and ease of deployment. The operation is very simple. Of course, you have to train someone in order to use it effectively. It's very easy to find training. For us, it's good to have a third party with enough experience in order to support other projects where we don't have enough people in order to do that.
I'd rate the solution at an eight out of ten.
Which deployment model are you using for this solution?
On-premises
Disclosure: I am a real user, and this review is based on my own experience and opinions.
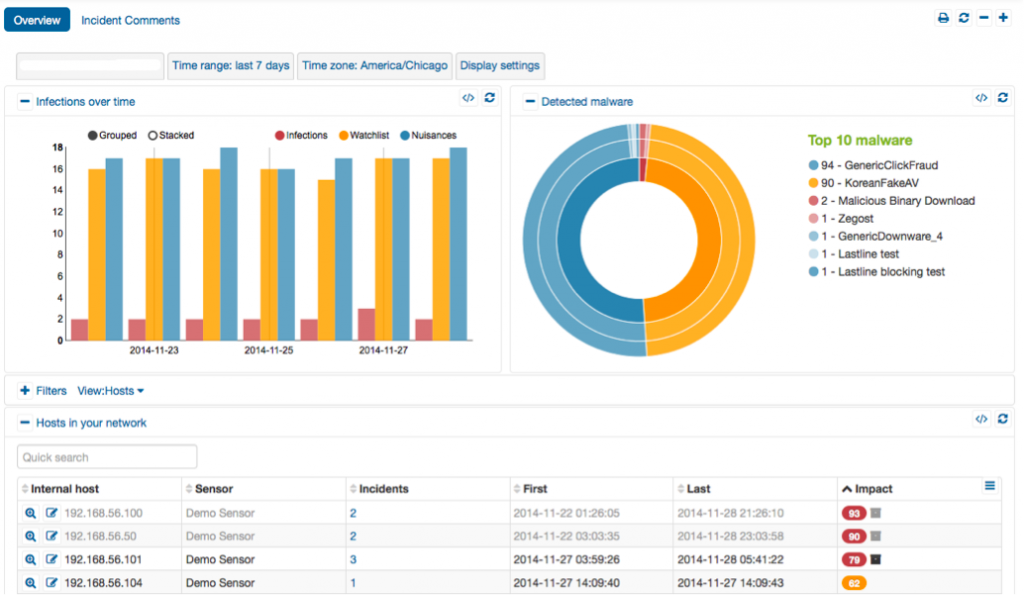 What is needed is a next-generation sandbox that can correlate a series of particular breach events add IP and object based reputation analysis and do this in near real-time. This is what the Lastline Breach Detection Platform does. What makes them unique is their range of discovery, the way they can effectively mimic actual PC or smartphone endpoints to examine malware behavior.
What is needed is a next-generation sandbox that can correlate a series of particular breach events add IP and object based reputation analysis and do this in near real-time. This is what the Lastline Breach Detection Platform does. What makes them unique is their range of discovery, the way they can effectively mimic actual PC or smartphone endpoints to examine malware behavior.
















