Security and protecting your IT environment is the biggest challenge now.
How to prevent ransomware attacks?
Part 1 described our approach to proactively protect your environment. The first step is to scan your environment from server to endpoint and check your complete environment on several issues preventing a hacker to penetrate your systems. Most of the times hackers getting a chance because of the complexity of IT. One thing your IT department forgets most of the time is, for example, the BIOS and the microcode. The first thing we do is discover all hardware, software, BIOS, Microcode, and the relationship with all those components. We have different options to do this. If you are a SMB environment a tool like Lansweeper is an excellent solution, it is not expensive and it will do the job.
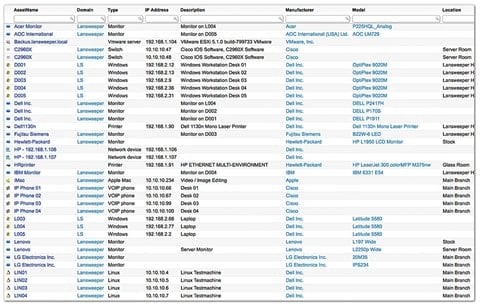
For bigger environments, we have different options: BMC Discovery, IBM TADDM. I will mention only BMC and IBM. You have many more. I do not have experience with other brands and describe only BMC and IBM.
I worked for a long time with IBM. For this solution I prefer BMC. It is easy to install and extremely easy to understand and work with it.
IBM Maximo Asset Management IBM Asset management software
IBM has a lot of different solutions but to cope with those threads and IT Complexity, IBM´s strategy is changing towards Artificial Intelligence. Also, from the Tivoli brand, you have TADDM.
Enterprise asset management (EAM) is a combination of software, systems, and services used to maintain and control operational assets and equipment. The aim is to optimize the quality and utilization of assets throughout their lifecycle, increase productive uptime and reduce operational costs.
Enterprise asset management involves work management, asset maintenance, planning and scheduling, supply chain management and environmental, health and safety (EHS) initiatives.
In the Internet of Things (IoT) era — with everything from valves to vehicles connected by sensors and systems — practitioners are incorporating advanced analytics and artificial intelligence (AI) into EAM. Data gathered from instrumented assets is analyzed using AI techniques. The resulting insights help maintenance teams make better decisions, enhance efficiency, perform preventive maintenance and maximize investments in their physical assets.

Now you have the asset management database, you know every application, every server, every hardware and software component, and the relationship.
So we can ask for example: are there endpoints with an old virus checker? Or how many systems are not on the right OS level? Bring all systems on the same anti-virus level or do I have any systems with an old BIOS level. If yes, then upgrade it to the same level as described in our policy template.






There are a number of discovery tools and security applications on the market today. Some of the more popular ones include:
- App discovery: Appthority, FindMyApp
- Email discovery: Code Factors, Microsoft Exchange Reporter, ProDiscover TX, SolarWinds MSP Mail Security
- Network discovery: BeyondTrust PowerBroker Auditor for Networks, Lancope StealthWatch Enterprise, NetFort LANGuardian
- Security information and event management (SIEM): AlienVault USM Anywhere, ArcSight ESM, IBM QRadar SIEM